Ssh Generate New Private Key
Sep 06, 2019 Generating your key pair and propagating your public key is simpler than it sounds. Let’s walk through it. Generating the key. The minimum effort to generate a key pair involves running the ssh-keygen command, and choosing the defaults at all the prompts: $ ssh-keygen Generating public/private rsa key pair. Add your SSH private key to the ssh-agent. If you created your key with a different name, or if you are adding an existing key that has a different name, replace idrsa in the command with the name of your private key file. $ ssh-add /.ssh/idrsa; Add the SSH key to your GitHub account. Jun 23, 2017 Once your public/private key are generated, place the public key in: /home/mynewuser/.ssh/authorizedkeys Download the private key locally and then remove both from the server as they are no longer needed. Use the ssh-keygen command to generate SSH public and private key files. By default, these files are created in the /.ssh directory. You can specify a different location, and an optional password (passphrase) to access the private key file. If an SSH key pair with the same name exists in the given location, those files are overwritten.
This version of GitHub Enterprise will be discontinued on This version of GitHub Enterprise was discontinued on 2019-03-27. No patch releases will be made, even for critical security issues. For better performance, improved security, and new features, upgrade to the latest version of GitHub Enterprise.For help with the upgrade, contact GitHub Enterprise support.

After you've checked for existing SSH keys, you can generate a new SSH key to use for authentication, then add it to the ssh-agent.
If you don't already have an SSH key, you must generate a new SSH key. If you're unsure whether you already have an SSH key, check for existing keys.
If you don't want to reenter your passphrase every time you use your SSH key, you can add your key to the SSH agent, which manages your SSH keys and remembers your passphrase.
Cisco ASA SSH, Don’t Forget To Generate A Key. Crypto key generate rsa modulus 1024: Filed under Cisco, Cisco ASA, Networking, Security. 6 Comments leave a comment. Iam8up / Aug 15 2011. The fact that Cisco doesn’t do this automatically makes me very very nervous. The networks running Cisco appear to be primarily using telnet =. Crypto key generate rsa modulus 1024 ip domain-name domain-name ip ssh version 2 ip ssh time-out 120 ip ssh authentication-retries 3 line vty 0 4 transport input telnet ssh end. Using GUI, ASDM, How can we generate crypto key modulus 1024? ASAXXX(config)# crypto key generate rsa general-keys modulus 1024 INFO: The name for the keys will be: Keypair generation process begin. Please wait.% Attempt to generate RSA keys failed. Now at command line you can fix this with a ‘Crypto Key Generate RSA Modulus 2048‘ command, but you can’t get to command line only ASDM. Solution On older versions of the ASDM you could generate the keypair in the Identification Certificates section (well you still can but only if you are also generating a certificate request file). Generate a rsa crypto key.
Generating a new SSH key
Open TerminalTerminalGit Bashthe terminal.
Paste the text below, substituting in your GitHub Enterprise email address.
This creates a new ssh key, using the provided email as a label.
When you're prompted to 'Enter a file in which to save the key,' press Enter. This accepts the default file location.
At the prompt, type a secure passphrase. For more information, see 'Working with SSH key passphrases'.
Adding your SSH key to the ssh-agent
Before adding a new SSH key to the ssh-agent to manage your keys, you should have checked for existing SSH keys and generated a new SSH key. When adding your SSH key to the agent, use the default macOS ssh-add command, and not an application installed by macports, homebrew, or some other external source.
Start the ssh-agent in the background.
If you're using macOS Sierra 10.12.2 or later, you will need to modify your
~/.ssh/configfile to automatically load keys into the ssh-agent and store passphrases in your keychain.Add your SSH private key to the ssh-agent and store your passphrase in the keychain. If you created your key with a different name, or if you are adding an existing key that has a different name, replace id_rsa in the command with the name of your private key file.
Note: The
-Koption is Apple's standard version ofssh-add, which stores the passphrase in your keychain for you when you add an ssh key to the ssh-agent.If you don't have Apple's standard version installed, you may receive an error. For more information on resolving this error, see 'Error: ssh-add: illegal option -- K.'
Add the SSH key to your GitHub account.
If you have GitHub Desktop installed, you can use it to clone repositories and not deal with SSH keys. It also comes with the Git Bash tool, which is the preferred way of running git commands on Windows.
Ensure the ssh-agent is running:
- If you are using the Git Shell that's installed with GitHub Desktop, the ssh-agent should be running.
If you are using another terminal prompt, such as Git for Windows, you can use the 'Auto-launching the ssh-agent' instructions in 'Working with SSH key passphrases', or start it manually:
Add your SSH private key to the ssh-agent. If you created your key with a different name, or if you are adding an existing key that has a different name, replace id_rsa in the command with the name of your private key file.
Add the SSH key to your GitHub account.
Start the ssh-agent in the background.
Add your SSH private key to the ssh-agent. If you created your key with a different name, or if you are adding an existing key that has a different name, replace id_rsa in the command with the name of your private key file.
Add the SSH key to your GitHub account.
Start the ssh-agent in the background.
Add your SSH private key to the ssh-agent. If you created your key with a different name, or if you are adding an existing key that has a different name, replace id_rsa in the command with the name of your private key file.
Add the SSH key to your GitHub account.
Further reading
- 'About SSH'
- 'Working with SSH key passphrases'
Several tools exist to generate SSH public/private key pairs. The following sections show how to generate an SSH key pair on UNIX, UNIX-like and Windows platforms.
Generating an SSH Key Pair on UNIX and UNIX-Like Platforms Using the ssh-keygen Utility
UNIX and UNIX-like platforms (including Solaris and Linux) include the ssh-keygen utility to generate SSH key pairs.
- Navigate to your home directory:
- Run the ssh-keygen utility, providing as
filenameyour choice of file name for the private key:The ssh-keygen utility prompts you for a passphrase for the private key.
- Enter a passphrase for the private key, or press Enter to create a private key without a passphrase:
Note:
While a passphrase is not required, you should specify one as a security measure to protect the private key from unauthorized use. When you specify a passphrase, a user must enter the passphrase every time the private key is used.
The ssh-keygen utility prompts you to enter the passphrase again.
- Enter the passphrase again, or press Enter again to continue creating a private key without a passphrase:
- The ssh-keygen utility displays a message indicating that the private key has been saved as
filenameand the public key has been saved asfilename.pub. It also displays information about the key fingerprint and randomart image.
Generating an SSH Key Pair on Windows Using the PuTTYgen Program
Ssh Generate New Private Keyboard
The PuTTYgen program is part of PuTTY, an open source networking client for the Windows platform.
Generate New Ssh Key Mac
Ssh Create New Private Key
- Download and install PuTTY or PuTTYgen.
To download PuTTY or PuTTYgen, go to http://www.putty.org/ and click the You can download PuTTY here link.
- Run the PuTTYgen program.
- Set the Type of key to generate option to SSH-2 RSA.
- In the Number of bits in a generated key box, enter 2048.
- Click Generate to generate a public/private key pair.
As the key is being generated, move the mouse around the blank area as directed.
- (Optional) Enter a passphrase for the private key in the Key passphrase box and reenter it in the Confirm passphrase box.
Note:
While a passphrase is not required, you should specify one as a security measure to protect the private key from unauthorized use. When you specify a passphrase, a user must enter the passphrase every time the private key is used.
- Click Save private key to save the private key to a file. To adhere to file-naming conventions, you should give the private key file an extension of
.ppk(PuTTY private key).Note:
The.ppkfile extension indicates that the private key is in PuTTY's proprietary format. You must use a key of this format when using PuTTY as your SSH client. It cannot be used with other SSH client tools. Refer to the PuTTY documentation to convert a private key in this format to a different format. - Select all of the characters in the Public key for pasting into OpenSSH authorized_keys file box.
Make sure you select all the characters, not just the ones you can see in the narrow window. If a scroll bar is next to the characters, you aren't seeing all the characters.
- Right-click somewhere in the selected text and select Copy from the menu.
- Open a text editor and paste the characters, just as you copied them. Start at the first character in the text editor, and do not insert any line breaks.
- Save the text file in the same folder where you saved the private key, using the
.pubextension to indicate that the file contains a public key. - If you or others are going to use an SSH client that requires the OpenSSH format for private keys (such as the
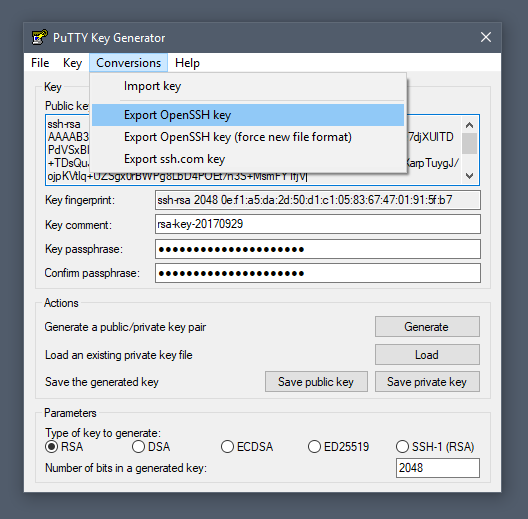
sshutility on Linux), export the private key:- On the Conversions menu, choose Export OpenSSH key.
- Save the private key in OpenSSH format in the same folder where you saved the private key in
.ppkformat, using an extension such as.opensshto indicate the file's content.