Generate Certificate From Private Key
At the prompt, change the Common Name to your client's domain name using the format client2.example.com. Leave all of the remaining fields as the default values.

Common OpenSSL Commands with Keys and Certificates. Generate RSA private key with certificate in a single command openssl req -x509 -newkey rsa:4096 -sha256 -keyout example.key -out example.crt -subj '/CN=example.com' -days 3650 -passout pass:foobar Generate Certificate Signing Request (CSR) from private key with passphrase. Generating a private key and self-signed certificate can be accomplished in a few simple steps using OpenSSL. We provide here detailed instructions on how to create a private key and self-signed certificate valid for 365 days.
Important: If you don't follow the format specified above for setting common names, the domain names aren't available when you import the certificate into ACM. As a result, the certificate isn't an available option for specifying the server certificate or client certificate when you create the AWS Client VPN endpoint.
Generate Public Certificate From Private Key
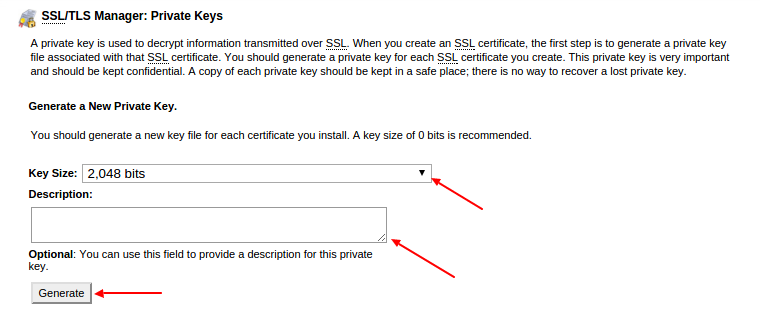
A missing private key could mean: The certificate is not being installed on the same server that generated the CSR. The pending request was deleted from IIS. The certificate was installed through the Certificate Import Wizard rather than through IIS. Select the private key that you wish to backup. Right click on the file and choose All Tasks Export 9. The certificate export wizard will start, please click Next to continue. In the next window select Yes, export the private key and click Next 10. Leave the default settings selected and click Next.
Import the server and client certificates and keys into ACM
Note: The server and client certificates, and their respective keys, are available in C:Program FilesOpenVPNeasy-rsakeys.
1. Open the following files: server.crt, server.key, client1.crt, client1.key, and ca.crt.
Create a PKCS#12 keystore from a private key and certificate OpenSSL is an open source software library that provides the pkcs12 command for generating PKCS#12 files from a private key and a certificate. With the private key, you can then generate the CSR: If you want to extract the public key from the CSR, all examples I've seen require the private key to be present in the openssl command: I assume CAs do something similar to sign the certificates and therefore create a public key.
2. Open the ACM console, and then choose Import a certificate.
3. On the Import a certificate page, copy/paste the content:
From the server.crt file to Certificate body.
From the server.key file to Certificate private key.
From the ca.crt file to Certificate chain.
Generate Pem Certificate From Private Key
4. Choose Import to import the server certificate.
5. Choose Import a certificate again and copy/paste the content:
From the client1.crt file to Certificate body.
From the client1.key file to Certificate private key.
From the ca.crt fileto Certificate chain.
Note: clBitCrack.exe is still EXPERIMENTAL, as users have reported critial bugs when running on some AMD and Intel devices.Note for Intel users:There is bug in Intel's OpenCL implementation which affects BitCrack. Using BitCrack UsageUse cuBitCrack.exe for CUDA devices and clBitCrack.exe for OpenCL devices. The main purpose of this project is to contribute to the effort of solving the: A transaction with 32 addresses that become increasingly difficult to crack. 
6. Choose Import to import the client certificate.
Or, you can use the AWS Command Line Interface (AWS CLI) to import the server and client certificates and their keys into ACM: